The hard numbers: what cybersecurity really costs
Cybersecurity costs real money, but it is now table-stackes. You simply have to pay the price to secure your company. It's the oxygen for the patient. The issues of data sensitivity, business continuity, regulation compliance, and customer trust are now all center-stage.
“Cybersecurity is not just a technical issue, it is also a business issue. The financial cost of cybercrime is staggering, and organizations must consider the potential impact on their revenue, reputation, and customer trust. The costs of cybersecurity breaches are not just financial; they can also include legal liabilities, regulatory fines, and lost business opportunities.”
Mark Weatherford, Chief Strategy Officer, National Cybersecurity Center
Cybersecurity is essential for companies to protect sensitive data, maintain business continuity, comply with regulations, safeguard against cyber threats, and protect customer trust. By implementing effective cybersecurity measures, companies can reduce the risk of cyberattacks and mitigate the potential impact of any breaches. Cyber breaches and attacks can bring companies to a standstill, and hence are one of the hottest topics in the tech world.
We routinely discuss the ramifications of ransomware threats, cybersecurity events, and the remote-working climate. Often, it can feel abstract. You read about immense breaches on the news and certainly understand the SolarWinds hack was serious. But, if it hasn’t fallen in your lap, how bad is it, really? Bad, we say, very bad. Understandably, though, without direct experience, it’s challenging to get a picture of the numbers.
Specifically, events, percentages, and cost-factors. How much, for example, is ransomware costing various industries? And malware? Who is affected after a successful social-engineering scheme? To help you understand, we’re going to highlight some of the hard numbers.
The Covid-19 pandemic added fuel to the fire
The primary reasons for the exploding IT and cybersecurity costs were natural consequences of the COVID-19 pandemic. Hackers exploited the creation of numerous new vulnerable targets in the form of newly remote workers. Woe betide the organization that opened their computer systems indiscriminately to accomodate them. Today, 94% of scam attacks are delivered through emails. All it takes is a small slip-up or human error to compromise even the most well-built cybersecurity infrastructure. There’s no sign of phishing scams slowing down either, considering they make up 80% of cyber-attacks.
With high-returns and easy pickings, it’s easy to see why threat actors were so eager to take advantage (and still are).

Adding the numbers above, we are talking about roughly $118 billion per year globally...
A breach can lead to significant dollar and reputational loss
For starters, time is essential. And every second counts. Industries and organizations are hit in multi-faceted ways like forms of phishing and social engineering scams that are a race against time to stop the thieves before they break into the proverbial safe.
Naturally, every organization and enterprise is hit differently (in the event of a breach). Costs can be significant in terms of financial losses and damage to an organization's reputation. The exact cost of a breach varies widely depending on a number of factors, including the size and complexity of the organization, the type of data stolen, and the extent of the breach. Here are some of the costs that organizations may incur after a cybersecurity breach.
Financial Costs
First off, it’s got to be money. $17,700 is lost per minute due to cyber-attacks or some form of cyber-crime. But breaking it down a bit, the total cost will include the hard labor costs of employees discovering and investigating the breach, notifying customers or clients, and providing credit monitoring or identity theft protection. Organizations may also face legal fees, fines, and penalties. For instance, there are threat actors demanding ransoms that are as small as $10 to $20, a quick cash-in scheme. Others, however, hold far more valuable information hostage which can hit the thousands, ignoring downtime. The majority of cyber-attacks have monetary gains as a driver to commit the attack.
Operational Costs
After a breach, organizations may need to shut down their systems temporarily to investigate and repair the damage. This can result in lost productivity and revenue.
Reputational Costs
A cybersecurity breach can damage an organization's reputation and erode customer trust, which can have a long-term impact on the business. Organizations may need to invest in marketing and PR campaigns to rebuild their brand. CEOs will have to show up on television or online media campaigns to assure the public their brand is to be trusted.
Regulatory Costs
Organizations may face fines and penalties for failing to comply with regulatory requirements related to cybersecurity.
Recovery Costs
Depending on the extent of the breach, organizations may need to invest in new systems and technology to prevent future attacks.
The fallout from a successful breach is devastating, capable of overturning entire business models due to the cost alone. For example, a company may not even have a full grasp of the damage since hackers routinely “plant” themselves on networks going unnoticed for weeks and even months. When they do deliver their payload, downtime follows after. If a business chooses to pay the ransom, it must also sustain brand damage since disclosing incidents is a law requirement.
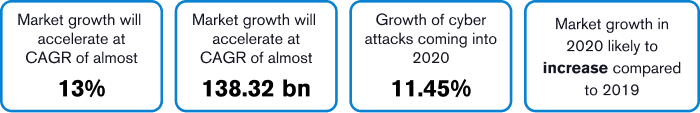
The Numbers
The global cybersecurity market in a few numbers:
The average cost of a cybersecurity attack
IBM took a hard look at cybersecurity breach costs by examining industries in the United States and all over the world. The average result of those costs wasn’t pretty. For the US, it took the highest average in expense costs, hitting around $8.64 million in damages. As for the worldwide average, IBM discovered the average cost was over $3 million USD. Those are some harrowing statistics, and you can imagine how a gargantuan cost factor puts an SMB in the ground if they were to suffer a breach of that scope.
The average amount of time it takes to detect an attack
Alarmingly, IBM’s report also found that the average time to discover and contain a breach was around 280 days. That’s more than half of a year - a heavy consequence indeed. It shows that even paying ransoms doesn’t end problems, and with subtle threats (as in threats that operate in the background or exploit misinformation), the act of defending a network is a painstaking, stressful, and time-consuming process adding to human labor and additional downtime.
Hospitals have been hit hard
The chaos created by the COVID-19 pandemic also developed a poisonous cyber environment for the medical industry. Regardless of the human cost, ransomware and malicious actors have been eager to exploit Coronavirus misinformation, routinely targeting hospital networks for a quick payday. In the US, then, hospitals were the most common target of social-engineering and malicious actors, which created an average of $7 million in damage costs. In 2020, the University of California San Francisco Medical Center paid a ransom of $1.14 million to regain access to its patient records and other important data, which had been encrypted by ransomware. In 2017, the WannaCry ransomware attack affected numerous healthcare organizations worldwide, including the National Health Service in the UK. The attack caused significant disruptions to patient care and highlighted the vulnerability of medical systems to cyber threats. In 2021, the Ireland's health service, HSE, suffered a ransomware attack that resulted in widespread system outages and the temporary closure of some services, including outpatient clinics and diagnostic imaging. In 2019, the American Medical Collection Agency (AMCA), a third-party collections agency for healthcare organizations, suffered a data breach that exposed the personal and medical information of millions of patients from various healthcare providers.
Schools and Universities are also being targeted
The education industry is also being hit by cyber / ransomware attacks. In 2021, (and 2022), the San Diego Unified School District suffered a ransomware attack that resulted in the shutdown of its computer systems and disrupted online learning for thousands of students. Commenting to a local news reporter was Sai Huda, a cybersecurity expert. He hinted that the students themselves are unfortunately being potentially targeted, in the form of identity theft.
“Now they can sell it [their personal information and credit] on the Dark Web and commits identity theft for all of these young that might not see the impact for many years.”
Sai Huda, Cybersecurity expert, CEO at CyberCatch
In 2020, the University of California Berkeley and Michigan State University both experienced cyber attacks that exposed personal information of students and staff, such as social security numbers and birthdates. In 2019, the Monroe-Woodbury Central School District in New York was hit by a ransomware attack that affected its computer systems and caused significant disruptions to its operations. In 2017, the Houston Independent School District suffered a data breach that compromised the personal information of employees, including names, social security numbers, and dates of birth.
The haunting history
While we hit on the contemporary spikes in cybersecurity costs and resources associated with it, the fact is cybersecurity and IT concerns have risen since 2016. While malware has always been “organic” to technological developments, complaints and ransomware have taken center stage.
In 2020, the FBI conducted a comprehensive report regarding trends, complaints, and costs they’ve observed since 2016. They compared them to 2020 and only saw the figures grow. For example, in 2016, there were roughly 298,728 cybersecurity complaints from various industries. The complaint here means a kind of breach or concern that involved cybersecurity and/or data breaches. In 2022, however, they received 791,790 complaints in total. Some of that, of course, is due to COVID-19, ransomware, and remote working, but it’s a red flag that security events are always increasing. Each year since 2016 saw those complaint figures rise by at least 50k.
Cost-wise, it’s uglier. In 2016, total costs were at $1.6 billion, another figure that’s only risen. In 2020, that figure swelled to a startling $4 billion (this figure involves all estimated cybersecurity costs related to threat events in the United States). That is a 25.7% annual growth rate. That’s in line with what we’ve talked about so far, and matches the surge of threat-activity related to remote working.
Unsurprisingly, while ransomware is the method of choice to hijack systems, phishing, and social engineering are the go-to delivery techniques. Once again, 2020 has clearly demonstrated how remote infrastructure fell under attack. For comparison, the FBI identified around 50,000 phishing report events back in 2016. In 2020, that figure rose to a herculean of 241,000. That, believe it or not, is a 48.2% annual growth rate. This, keep in mind, is what’s reported. There are still likely threat events and intrusions not reported, and, these are only US-specific statistics.
Tame the cybersecurity breach beast using data
You can smell the money burning with the explosion of cyber-attacks. It can easily leave the hardiest business in a despairing state. What if you fall victim to a massive cyber-attack or ransomware intrusion? Do you have the resources to cover the costs, fallout, and rebuild brand strength? Like a bad hospital visit, it can be a life-altering event.
But there is a kernel of optimism in this sea of information, and that is data. Data can be a powerful tool in the fight against cyber threats. By collecting and analyzing data on past and current threats, organizations can develop a better understanding of their security risks and take proactive steps to prevent attacks.
Here are some of the ways that organizations can reduce cyber-attacks using data:
Threat Intelligence
By gathering and analyzing data on past and current cyber threats, organizations can develop a better understanding of the types of attacks they are likely to face and take steps to prevent them. Threat intelligence can include information on known vulnerabilities, malware samples, and indicators of compromise.
User Behavior Analytics
By analyzing data on user behavior, organizations can detect unusual or suspicious activity that may indicate a potential attack. User behavior analytics can help identify compromised accounts, insider threats, and other security issues.
Log Analysis
By analyzing logs from various sources, including network devices, servers, and applications, organizations can detect and respond to security incidents more quickly. Log analysis can help identify patterns of suspicious activity, track the movement of attackers within the network, and provide forensic evidence after an attack.
Machine Learning
By using machine learning algorithms to analyze data, organizations can identify patterns and anomalies that may indicate a potential attack. Machine learning can be used to detect malware, phishing attempts, and other security threats.
Big Data Analytics
By analyzing large volumes of data from multiple sources, organizations can gain a more comprehensive view of their security posture and identify potential vulnerabilities. Big data analytics can help identify patterns and trends that may be missed by traditional security solutions.
Threat Hunting
By proactively searching for threats within their networks, organizations can identify and eliminate potential security issues before they are exploited. Threat hunting can involve using a combination of data analysis and human intuition to identify suspicious activity and potential threats. For example, you can absolutely see how phishing, social engineering, and fraud emails remain the most popular delivery method for threat actors. That means you can feel comfortable investing defensive resources to thwart those attacks. Obviously, you can’t keep track of every single malware strain and every single threat, but you have a clear picture of what malicious parties attempt to do and their preferred methods.
Closing thoughts
The number and sophistication of cyber threats are increasing, with attackers constantly developing new techniques and tools to bypass security measures. For the foreseeable future, it’s unlikely cybersecurity costs will go down. Even if ransomware threats and other malicious activities are curtailed by government policy, the cost structure will increase.
Organizations need to stay ahead of these threats by investing in advanced security solutions and services. The best thing any major enterprise can do is mind these trends and allocate the necessary resources. Doing so will prevent financial calamity and help them adapt to the modern cybersecurity markets.
Progressive organizations must invest time and resources in building a robust quick action plan in the event of a cyber-attack. Should one occur, it's important to take immediate action to minimize the damage and protect your organization's assets. Damage control in case of an attack involves containing the attack, assessing the damage, notifying relevant parties, preserving evidence, remediating the attack, restoring systems and data, and reviewing and improving security. By taking the right steps in a timely manner, organizations can minimize the impact of a cyber-attack and prevent future attacks.
Takeaways
By utilizing these available advanced tools, organizations can stay one step ahead of cyber criminals and reduce their risk of falling victim to a cyber attack. An important principle is that an ounce of prevention is worth a pound of cure
- Building up a threat intelligence business is key. By gathering and analyzing data on past and current cyber threats, organizations can develop a better understanding of the types of attacks they are likely to face and take steps to prevent them.
- Monitoring user behavior and network activity to detect abnormal behavior that may indicate a cyber attack in progress.
- Use machine learning and ai algorithms to analyze large amounts of data in real-time to identify patterns and anomalies that may indicate a cyber attack.
- Deploy your own security information and event management (SIEM). SIEM tools can be used to collect and analyze security-related data from across an organization's network, including logs, event data, and alerts from security devices.
- Go on a threat hunting expedition. This involves actively searching for potential cyber threats within an organization's network. This can be done using a combination of manual techniques and automated tools, such as machine learning algorithms and SIEM.
- Train your users not to click on emails or text message links. There are so many technically illiterate users on your network, (on all networks), that will click on SPAM emails and SPAM text messages to unleash all manner of evil viruses in your network. These staff members need to be aggressively trained and protected from their own naivete and lack of sophistication, or they will spell doom for your IT systems and cost your organization countless millions.









